In a new fashion for stealing cars, automotive security experts have discovered that cybercriminals can hack into a vehicle’s control system through the headlight. The control system is managed by the controller area network (CAN) bus, an Internet of Things (IoT) protocol that allows devices and microcontrollers to communicate with each other within the car.
By manipulating the electronic control unit (ECU) in a Toyota RAV4’s headlight, attackers could access the CAN bus and gain control of the car. This approach, as described in a blog post by Canis Automotive Labs CTO Ken Tindell, is a unique way of car hacking that had not been seen before. Once connected through the headlight, the attackers could gain access to the CAN bus, responsible for functions like the parking brakes, headlights, and smart key, and then into the powertrain panel where the engine control is located.
Even though car hacking is not a new issue, this method of attack highlights the vulnerability of IoT protocols like the CAN bus and the need for improved security measures in automotive systems.
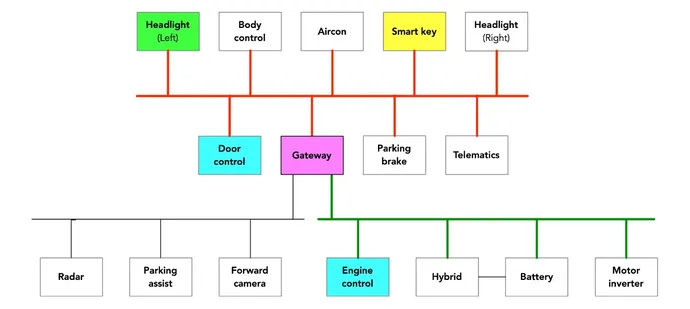
Connecting ECUs in a RAV4 using CAN Bus Wiring (via Canis CTO blog)
Tindell cautions that this form of CAN injection will compel manufacturers to reconsider the security of their vehicle control networks. “As a car engineer, your focus is on addressing a variety of challenges such as minimizing wiring, enhancing reliability, and reducing costs. Cybersecurity may not always be at the forefront of your mind.”
A Case of Stolen Toyota RAV4 in London
Ian Tabor, an automotive security consultant, woke up to discover that his parked Toyota RAV4 had been tampered with in London. The car’s front bumper and left headlight had been disturbed, and the same areas were later found to be tampered with again.
https://twitter.com/mintynet/status/1518274535035965440?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1518274535035965440%7Ctwgr%5E%7Ctwcon%5Es1_&ref_url=safari-reader%3A%2F%2Fwww.darkreading.com%2Fattacks-breaches%2Fcybercriminals-can-steal-your-car-novel-iot-hack
Unfortunately, he didn’t realize the extent of the sabotage until his vehicle was stolen. Surprisingly, Tabor’s friend and automotive engineer, Tindell, who had previously developed a CAN-based platform for Volvo, was in a position to assist, as the RAV4’s vulnerability was traced to its CAN system. The incident highlights the urgent need for improved vehicle cybersecurity.
https://twitter.com/mintynet/status/1549955820166778881?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1549955820166778881%7Ctwgr%5E%7Ctwcon%5Es1_&ref_url=safari-reader%3A%2F%2Fwww.darkreading.com%2Fattacks-breaches%2Fcybercriminals-can-steal-your-car-novel-iot-hack
The “Key” to Car Break-Ins
According to Tindell, the key to breaking into modern vehicles is, in fact, the key itself. The wireless key acts as a perimeter defense that communicates with the engine control unit (ECU) to verify its authenticity before allowing the engine immobilizer to start the car. Thieves commonly use “relay attacks,” which involve using a handheld radio relay station to intercept the car’s authentication request and relay it to the smart key, usually located in the owner’s home.
Manufacturers have countered this by designing keys to “go to sleep” after a couple of minutes of inactivity, and owners with keys that don’t do that can store them inside radio-impenetrable metal boxes. Other attack methods include exploiting vulnerabilities in mobile apps and infotainment systems.
Filed in . Read more about Cars and IoT (Internet of Things).