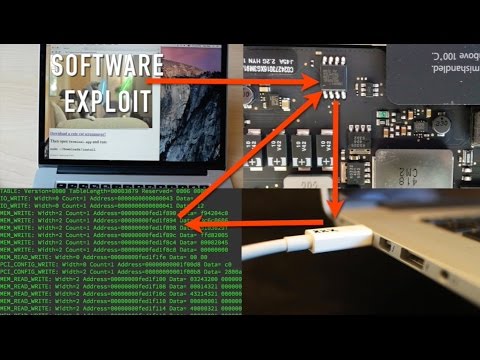
Researchers Create First Firmware Worm That Can Infect Macs
Some of you guys might recall that a couple of months ago, an exploit nicknamed Thunderstrike was discovered for Mac computers, where basically it could allow hackers to modify the firmware of a Mac computer. Further proving the vulnerability and bringing it to attention, a group of researchers have built on that exploit, resulting in Thunderstrike 2.
According to a report from WIRED, it seems that Thunderstrike is basically a worm that can infect the firmware of a Mac computer, thus making it impossible to be removed. Issuing a patch would be impossible since the worm is said to be able to block the update or reinstall itself regardless of what’s been done.
The scary thing about Thunderstrike 2 is that it can easily infect a Mac computer via a website or email, and it will also be able to spread itself to other Mac computers by hiding in the option ROM of peripherals such as Thunderbolt or a Gigabit Ethernet adapter, external drives, RAID controllers, and more.
To fix the issue, it seems that it can only be done at a hardware level, meaning that the average user probably won’t know what to do about it. According to the researchers, “Some vendors like Dell and Lenovo have been very active in trying to rapidly remove vulnerabilities from their firmware. Most other vendors, including Apple as we are showing here, have not. We use our research to help raise awareness of firmware attacks, and show customers that they need to hold their vendors accountable for better firmware security.”
The researchers have since gotten in touch with Apple, but the Cupertino company has so far only fixed one of the five security flaws they pointed out, and have only partially addressed the second, but hopefully they will be fixed in future updates. Hopefully in the meantime hackers don’t take advantage of this and start infecting Mac computers with this worm.
You May Also Like
Popular Right Now
- WhatsApp Introduces Voice Chats For All Groups, Inspired By Telegram
- Volonaut Airbike: Lightweight Flying Superbikes With Jet Propulsion Unveiled
- Flappy Bird Is Back! After 10 Years, It Brings A New Game Experience
- Google Messages Rolls Out On-Device Nudity Detection With Sensitive Content Warnings
- Google AI Mode Adds Multimodal Search To Mobile App
- Leaked Apple Watch Series 10 Prototype Reveals Unique Health Sensor And Potential Future Features
- Canon Unveils PowerShot V1 And EOS R50 V: Best New Vlogging Cameras For 2025
- Bill Gates Predicts: AI Will Replace Doctors And Tutors Within A Decade
- First Shutdown of Niagara Falls in 12,000 Years: A Rare Sight to Behold
- Former Google Engineer claims that humans will achieve immortality soon
- Romotow: The Foldable Camping Trailer Inspired By A USB Flash Drive
- LYRA: Swiss Startup Unveils AR Smart Glasses for Office Work, City Life, And Traveling
- Man Caught in China Smuggling $46K Worth of Intel CPUs Wrapped Around His Waist
- iPhone 15 Pro Max may bring thinner bezels than Xiaomi and Samsung’s latest flagships
- OpenAI's new GPT-4 with a "human-level performance" scored up to 93% on SAT exams
- iPhone SE 4 could be Apple's secret weapon to 'steal' budget customers from Samsung